Zero Trust
Never Trust, Always Verify
What is Zero Trust?
A Zero Trust model is a security concept that assumes that no user, device or process, whether inside or outside the network, is automatically trustworthy. It is based on the idea that all access attempts must be strictly checked and authorized, regardless of their origin or position. Zero Trust uses continuous checks and authentication to minimize potential threats and improve security.
How does Zero Trust differ from conventional security concepts?
Zero Trust revolutionizes the way in which security in networks is viewed. The conventional trust-based model is put to the test – instead, consistent checks and controls are used to enhance network security.
Conventional security approaches often rely on securing the network perimeter with firewalls and other security solutions. Once an attacker or malicious insider has breached this outer security layer, they can move laterally within the entire network undetected, access sensitive data, compromise further systems and increase the impact of the attack. Defensive measures become more difficult and the extent of potential damage increases.
Why is Zero Trust necessary?
The widespread popularity of mobile working and cloud services has resulted in highly distributed, dynamic IT environments, making it increasingly difficult to detect and defend against advanced cyberattacks.
Conventional technical security measures like firewalls, malware scanners and URL filters are no longer enough to protect critical IT or OT business processes appropriately.
Zero Trust in practice
In a Zero Trust model, there are no devices or interfaces that are fundamentally trustworthy, nor are network segments defined statically as secure or unsecure. Instead, a security policy is used to dynamically decide whether an end device or user is trustworthy. Adherence to this policy is constantly monitored so that any violations can be detected immediately and mitigated (automatically) where necessary.
Using advanced technologies like security service edge (SSE) and Zero Trust network access (ZTNA) enables this comprehensive security level to be implemented even in modern workplace concepts. At the same time, this also makes distributed IT services very user friendly.
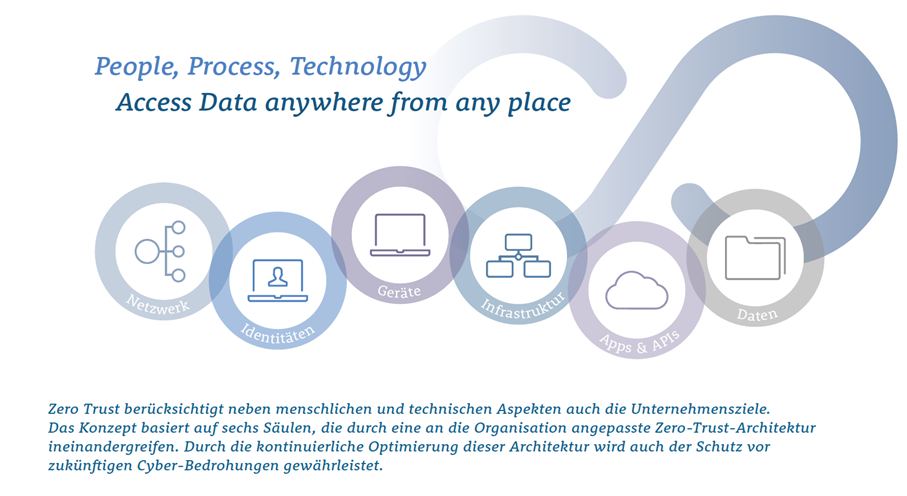
A Zero Trust architecture is a comprehensive and adaptable architecture designed to increase resilience to cyberthreats such as ransomware or targeted attacks. Once such an architecture has been designed and implemented successfully, access to IT services can also be made more user friendly.
We look forward to supporting you in planning and implementing your Zero Trust architecture.
Any Questions?
If you would like to know more about this subject, I am happy to assist you.
Contact us
